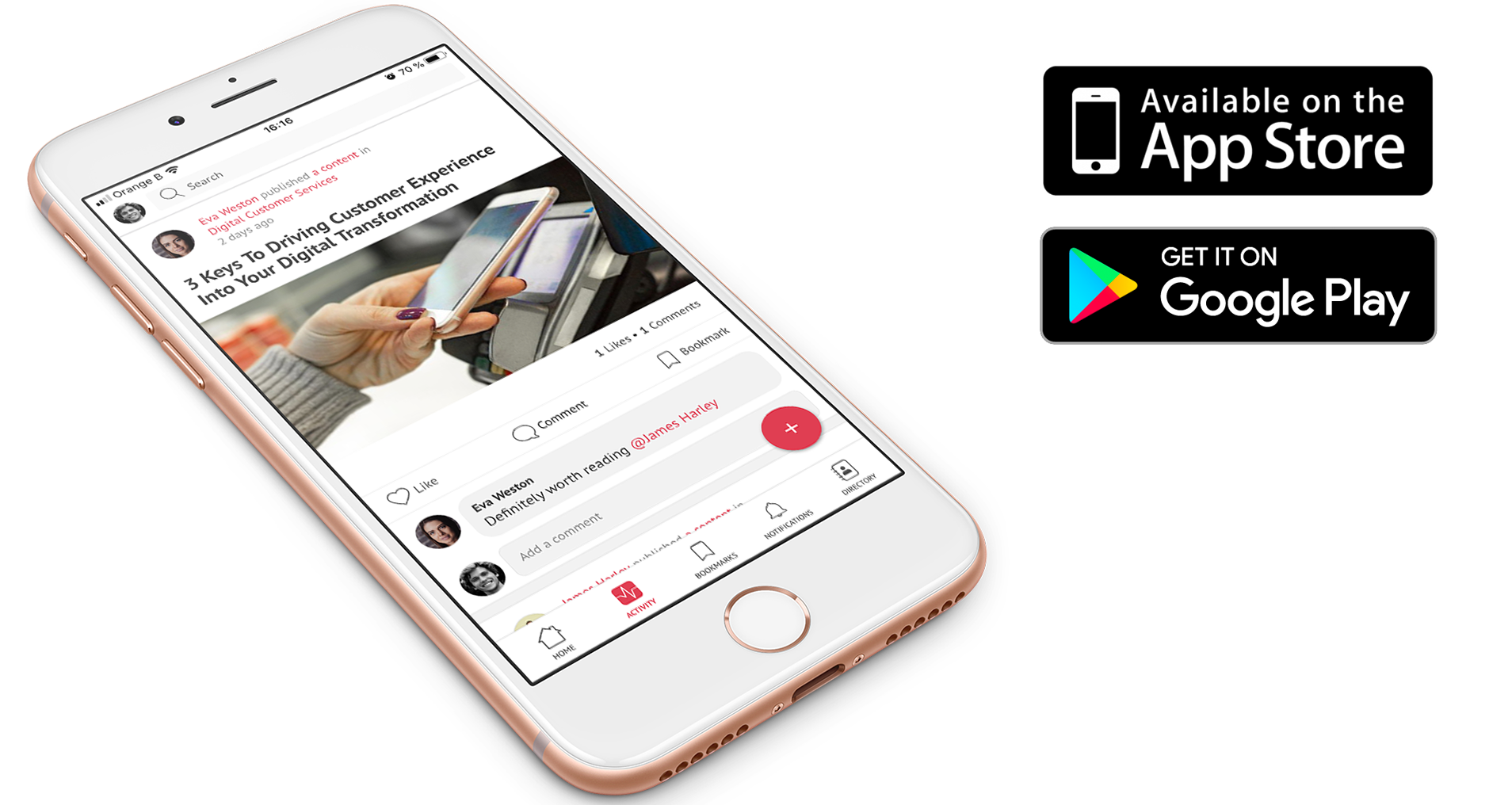
State-of-the-art sharing experience, even on the go, with Elium's mobile app
At the office, visiting a client, or when attending a business conference – your employees can share and digest key company knowledge wherever you are.
They get the same level of experience as on desktop, while enjoying the highest standards of security.

Best in class user experience
Elium offers the same sharing experience on mobile, as on desktop. Knowledge sharing is easy and intuitive.

Enterprise-graded security
Never worry about sharing safely. Elium’s mobile app offers biometric and code-based authentification.

Knowledge available even when offline
Connected every time. Users can bookmark content and access it even when no internet is available, like during flights.

AI Assistent to keep content relevant
Every few visits, the AI Assistent gives users smart suggestions essential to keep the platform’s content relevant.
See how it works 👇
Brand it as you wish to ensure user's engagement 

For the Enterprise plan, Elium allows you to personalise the mobile app, in link with your company’s branding.
This can help boost usage and engagement.
- Chose the best name for your app: It can be your company’s name or a brand that you create for this project. Ensure it speaks to your teams.
- Select the right colours: This will help users to better recognise, find the app in the store and identify with it.
Frequently asked questions
Data Availability
YES. We have an historic uptime of 99.9% or higher. We monitor our uptime using Pingdom and our services resources utilisation with Datadog.
YES. Elium was built with disaster recovery in mind. All of our infrastructure and data are spread across multiple GCP availability zones in Europe. Provisioning of our services are scripted and can be restored in less than 1 hour in any other Cloud data center in case of major issue on the primary data-center.
Hosting
YES. your data is private and safe at all times. Elium complies with the highest standards of data protection, following the GDPR requirements released in 2018 in Europe.
We are an independent and GDPR-compliant vendor established in 2008 in Belgium. Our whole infrastructure, customer data and backups are entirely managed by our engineering teams and exclusively hosted within highly secured ISO27001, SOC1/2/3, Tier-4 facilities in Europe. Our security and privacy policies (including third parties we work with) can be reviewed here. For any potential concerns, you can reach out to [email protected]
YES. EYES. Elium services and data are hosted in Europe. We provide 2 cloud hosting solutions:
- Google Cloud Platform, and most specifically region eu-west1 (Belgium) for services and mutli-region EU (Belgium, Netherlands, Finland, Germany) Cloud storage for data.
- 3DS Outscale, using SecNumCloud regions (Paris, France) for services and data.
Privacy Processes
YES. All of our services are within our own containers cluster (Kubernetes) with network access control lists (ACLs) that prevent unauthorized requests getting to our internal network.
YES. We have a process related to logging and tracing. On an application level, we produce audit logs for all activity, ship logs to Datadog for analysis and use S3 for archival purposes. All actions taken on production consoles or in the Elium application are logged.
YES. We regularly update systems and services that operate Elium and apply security patches when required. We manage any modification through a change management system that allows us to quickly revert these in case of unattended issues.
Security Features
YES. Elium provides three password levels complexity and credentials are stored using a hashing and salting functions (bcrypt).
YES.. All data sent to or from Elium is encrypted in transit using 256 bit encryption. Our API and application endpoints are TLS/SSL only and score an “A+” rating on Qualys SSL Labs‘ tests. This means we only use strong cipher suites and have features such as HSTS and Perfect Forward Secrecy fully enabled. We also encrypt data at rest using an industry-standard AES-256 encryption algorithm.
YES. We enable permission levels and access rights within the app to be set for your usage. Easy and secure gouvernance is one of the most appreciated features of Elium.
YES. Our product offers a standard protection against malware and virus. Once the option is activated, any image or file below 500 MB uploaded on Elium will be automatically screened for viruses using the ClamAV software.